The Data Availability and Transparency Act 2022 (the Act) sets out the responsibilities of DATA Scheme entities in relation to data breaches under the DATA Scheme. This guidance is being provided in line with the National Data Commissioner’s Regulation and Compliance Priorities (Priority 3 – Educate and guide on best practice data handling and sharing).
DATA Scheme entities have two key responsibilities in the event of a data breach under the Act (Scheme data breach):
- mitigate harm from the breach (see section 36 of the Act)
- notify the National Data Commissioner (the Commissioner) and the data custodian about the breach (see sections 31, 37 and 38 of the Act).
This guidance note supports DATA Scheme entities to mitigate harm from Scheme data breaches by providing guidance on:
- Recognising a Scheme data breach
- Preventing and preparing for Scheme data breaches
- Responding to Scheme data breaches.
What is a Scheme data breach?
A Scheme data breach is where a DATA Scheme entity (i.e. a data custodian, accredited user or accredited data service provider) holds Scheme data and one or more of the following occurs:
- there is unauthorised access to or disclosure of the Scheme data
- the data is lost in circumstances where there is likely to be unauthorised access to or disclosure of the data, or
- an event prescribed by a data code occurs in relation to the data. No such code exists yet.
A DATA Scheme entity does not have to establish whether or not a data breach incident involves personal information and/or would likely result in serious harm, for it to be a Scheme data breach. This is illustrated in Figure 1 below.
Figure 1: Scheme data breach
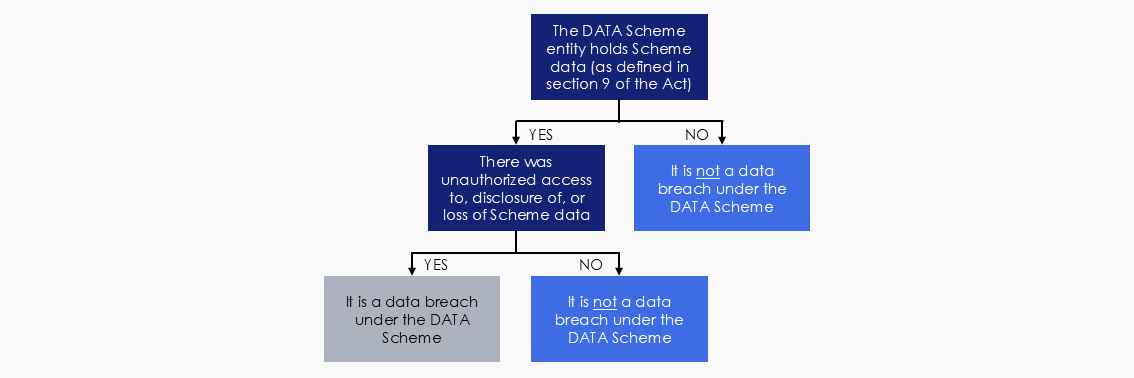
The DATA Scheme entity holds Scheme data
An element of a Scheme data breach is that the DATA Scheme entity holds Scheme data (see section 35(a) of the Act).
A DATA Scheme entity is taken to hold Scheme data if the entity has possession or control of a record that contains the data (see section 9 of the Act).
Under the DATA Scheme, ‘Scheme data’ means (see section 9 of the Act):
- any copy of data that has been created for the purpose of being shared under the DATA Scheme (irrespective of whether or not the data has yet been shared)
- accredited data service provider-enhanced data of a project, or
- output of a project.
A copy of data that has exited the Scheme ceases to be Scheme data (see section 20E of the Act).
Examples of Scheme data include a new data set created by a data custodian to be shared with an accredited user under the DATA Scheme, data that has been de-identified by an accredited data service provider as part of a data sharing agreement but has not yet been shared, and data collected by the accredited user as part of a data sharing project.
Unauthorised access to, disclosure of, or loss of Scheme data
In addition to a DATA Scheme entity holding Scheme data, there must be unauthorised access to, disclosure of, or loss of the data for a data breach to occur (see section 35(b) of the Act).
Unauthorised access
‘Unauthorised access’ occurs where Scheme data that a DATA Scheme entity holds is accessed by an individual who does not have permission to access the data. For example, a cyber attack could result in unauthorised access to Scheme data held by an accredited user.
Unauthorised disclosure
An ‘unauthorised disclosure’ occurs where:
- Scheme data is made accessible or visible where it is not authorised by the Act, and
- the Scheme data that is held by the DATA Scheme entity is released from the DATA Scheme entity’s effective control in a way that is not permitted by the Act.
For example, a disclosure of Scheme data to an employee or contracted third party who is not part of a data sharing project would be an unauthorised disclosure.
Loss
A data breach can also occur due to a loss of Scheme data, and the loss is likely to result in unauthorised access to, or disclosure of, Scheme data. This includes:
- Physically losing Scheme data – a loss could occur from data spills or circumstances in which an employee of a DATA Scheme entity accidentally leaves hard copy documents containing Scheme data in a public place where other individuals can easily access the data
- Electronically losing Scheme data – a loss could occur from failing to keep adequate backups of Scheme data in the event of a systems failure.
Scheme entity responsibilities in the event of a data breach
In the event a Scheme data breach, DATA Scheme entities have responsibilities under the Scheme. These responsibilities enliven when DATA Scheme entities reasonably suspect or become aware that a Scheme data breach has occurred. These responsibilities are captured in Figure 2 below.
Figure 2: Scheme entity responsibilities during a data breach
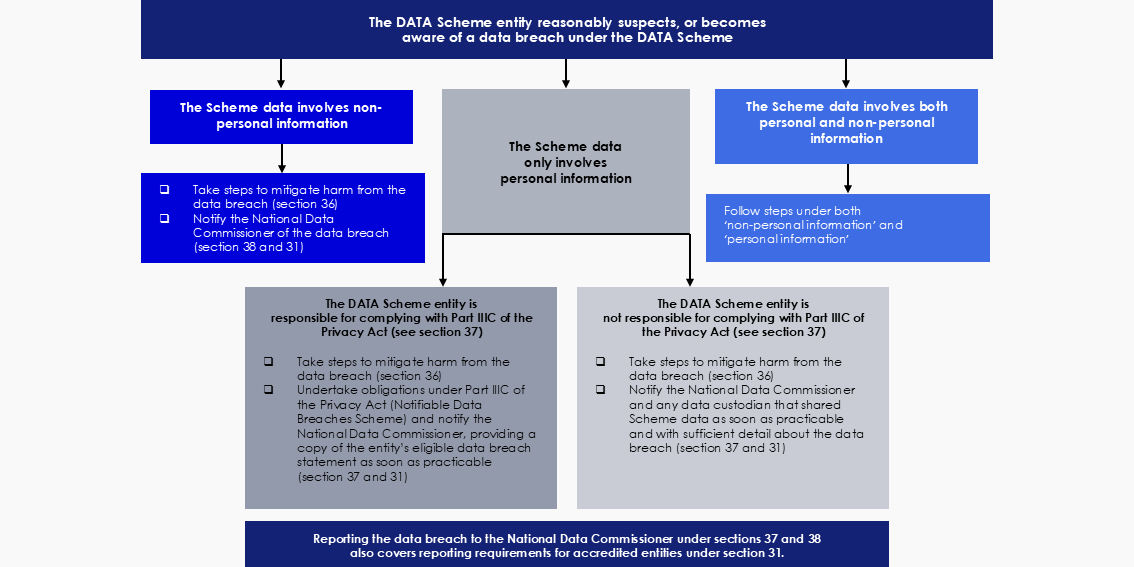
Preventing and preparing for Scheme data breaches
This guidance broadly aligns and should be used in conjunction with guidance prepared by the Office of the Australian Information Commissioner (OAIC) and the Australian Signals Directorate (ASD) about preparing for and responding to data breaches.
Data breaches can have a detrimental impact on individuals, businesses, other entities and national security. By implementing five steps to prevent and prepare for data breaches, DATA Scheme entities will minimise the risk of a data breach and any resulting harm. This is illustrated in Figure 3 below.
Figure 3: Steps to prevent and prepare for data breaches
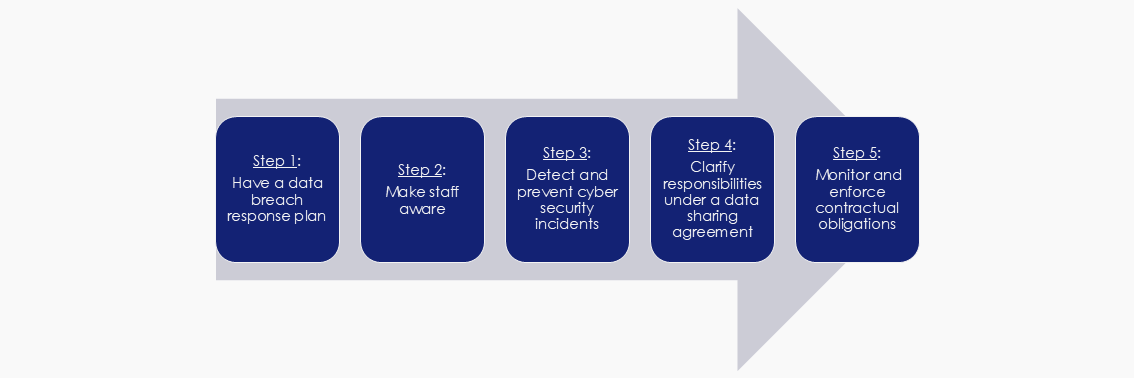
Five steps to prevent and prepare for data breaches
DATA Scheme entities should have a plan to respond to Scheme data breaches. A plan enables DATA Scheme entities to identify and respond quickly in the event of a Scheme data breach to mitigate harm, meet responsibilities under the Act, as well as maintain and build public trust in the entity and the DATA Scheme. DATA Scheme entities should update existing data breach response plans (including plans dealing with data breaches involving personal information) or develop a separate plan for Scheme data breaches. Topics and information that should be included in a plan for responding to Scheme data breaches are outlined in Table 1.
Table 1: Topics and information for a Scheme data breach response plan
| Topic | Information |
|---|---|
| Define ‘data breach’ under the DATA Scheme |
|
| Strategy to contain, assess and manage data breaches |
|
| Roles and responsibilities of staff |
|
| Document |
|
| Review |
|
Useful resources For further guidance on how to prepare a response plan, see OAIC guidance: Part 2: Preparing a data breach response plan and the ASD's Guidelines for Security Documentation. For resources or to seek advice and assistance in relation to cyber security incidents, visit www.cyber.gov.au. |
Staff should be supported to have the skills and capability to prevent, identify, report, and respond appropriately to suspected or identified Scheme data breaches. Recommended actions for DATA Scheme entities include:
- updating and making mandatory privacy and cyber security awareness training, particularly for staff who handle Scheme data
- making refresher training mandatory and providing it to staff on a regular basis
- not overlooking first principles prevention awareness in staff training, such as ensuring that screen recording and screen sharing does not result in unauthorised access to or disclosure of Scheme data
- making DATA Scheme entities’ responsibilities in the event of the Scheme data breach a focus during awareness-raising opportunities such as Privacy Awareness Week
- making the data breach response plan easily accessible to all staff and involving staff in data breach simulations to test the plan.
Useful resources The OAIC have developed training resources, which can be incorporated into staff training and refreshers. For privacy research and training resources from the OAIC, refer to Research and training resources | OAIC ASD provides cyber security advice and assistance to the whole of the Australian economy, which includes Australian Governments at the federal, state, territory and local levels, business and critical infrastructure. For more information about cyber security, see ASD's resources: Resources for business and government | Cyber.gov.au |
DATA Scheme entities should review their Scheme data holdings and update their data governance policies and processes to cover Scheme data. A clear understanding of the nature, purpose and location of Scheme data holdings will guide implementation of appropriate cyber security protections, in line with the risk profile of the data. The ASD’s guidance on strategies to mitigate cyber security, and the OAIC’s Guide to securing personal information provide further guidance on securing data consistent with a risk-based approach.
DATA Scheme entities should conduct and regularly review risk assessments to identify the level of protection required from various cyber threats and implement appropriate mitigation strategies. For example, DATA Scheme entities should be aware of the data breach landscape and consider how it may impact on risk assessments.
Useful resources For more information about detecting cyber security incidents, see ASD guidance: Guidelines for Cyber Security Incidents | Cyber.gov.au For guidance on strategies to mitigate cyber security incidents that may result in a data breach, see ASD guidance: Strategies to Mitigate Cyber Security Incidents | Cyber.gov.au For more information about securing personal information, see OAIC guidance: Guide to securing personal information | OAIC For guidance about undertaking privacy impact assessments, see OAIC guidance: Guide to undertaking privacy impact assessments | OAIC |
A data sharing agreement under the DATA Scheme must specify, amongst other things, how the project will be consistent with the data sharing principles (see section 19(7) of the Act). The people, setting and data principles in particular support DATA Scheme entities to minimise the risk of unauthorised access to, disclosure of, or loss of Scheme data.
Issues DATA Scheme entities should consider when collaborating on a data sharing agreement include:
- actions the parties will take to give effect to the people, setting and data principles (see sections 16 of the Act, and requirements that must be taken into account under Part 2 of the Data Availability and Transparency Code 2022)
- sharing the data through an accredited data service provider, and/or using data services (i.e., de-identification or secure access) to reduce the risk of a data breach (see section 16C of the Act)
- which entity will be responsible for satisfying the assessment and/or notification requirements in Part IIIC of the Privacy Act, where each entity that is a party to a data sharing agreement is an Australian Privacy Principles (APP) entity and reasonably suspects or becomes aware of a data breach under the DATA Scheme that involves personal information (see sections 19(12) and 37(2)-(4) of the Act), and
- whether additional data breach responsibilities should be included as part of the agreement to minimise the risk of data breaches in the particular data sharing project (see section 19(12A) of the Act).
Parties to a data sharing agreement should be clear on their data breach responsibilities under the particular data sharing agreement, including how they will work together with other parties to ensure quick and effective action in the event of a data breach.
Useful resources For more information about using an ADSP, see the Commissioner's guidance note: Using an Accredited Data Service Provider (ADSP) | Office of the National Data Commissioner |
In some cases, a DATA Scheme entity may have an approved contract with a third party (i.e., an individual or body corporate) that is authorised by, or approved under, a data sharing agreement (see section 123(3) of the Act) to provide services relating to the data sharing project.
DATA Scheme entities should ensure that any approved contracts with individuals or bodies corporate make clear obligations relating to data breaches involving data held by third parties as a result of the contract. Contractor obligations include, but are not limited to:
- taking all reasonable steps to mitigate the risk of data breaches
- immediately containing a Scheme data breach
- promptly notifying the DATA Scheme entity it is contracted with when a data breach occurs
- undertaking a prompt and effective assessment of a data breach incident, unless otherwise directed by the DATA Scheme entity.
DATA Scheme entities should consider clarifying contractual obligations in relation to Scheme data breaches. This includes inserting an APP-equivalence term into a data sharing agreement, where appropriate, that prohibits an entity from collecting or using personal information under the agreement in any way that would breach an Australian Privacy Principle (see section 16E (2) of the Act).
Contract managers should proactively monitor and enforce these contractual obligations. DATA Scheme entities should conduct regular internal audit and quality assurance activities to ensure contractual compliance.
If a DATA Scheme entity reasonably suspects that another DATA Scheme entity has failed to comply with the data sharing responsibilities under the Act or a data sharing agreement to which both entities are party, the entity may make a scheme complaint to the Commissioner (see section 88 of the Act).
Useful resources For more information about approved contracts, see the Commissioner's guidance note: Designated Individuals | Office of the National Data Commissioner For more information about Scheme complaints, see the Commissioner's guidance note: Handling complaints under the DATA Scheme | Office of the National Data Commissioner |
Responding to Scheme data breaches
When a DATA Scheme entity suspects or becomes aware of a data breach, it should activate its response plan and follow four steps. This is illustrated in Figure 4 below.
Figure 4: Steps to follow when an entity suspects a data breach
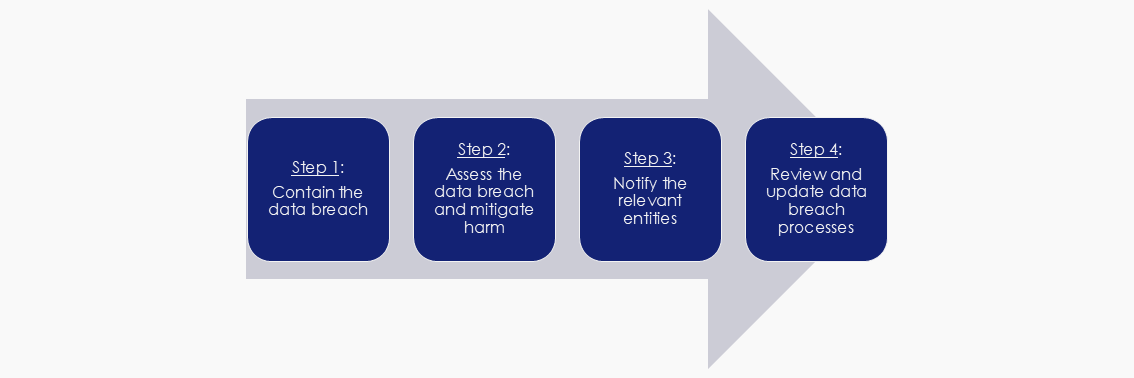
The steps draw from the OAIC's data breach preparation and response plan guidance in relation to the NDB Scheme, but have been amended to reflect the requirements of the DATA Scheme.
Four steps to follow when responding to Scheme data breaches
When a DATA Scheme entity reasonably suspects or becomes aware of a data breach within its entity, it must take reasonable steps to prevent or reduce any harm arising from the breach to entities, groups of entities and things (see section 36(1) of the Act).
A data custodian also has responsibility to take steps to mitigate harm if it reasonably suspects or becomes aware a data breach has occurred within an accredited user or accredited data service provider (ADSP), where Scheme data it has shared may be involved (see section 36(2) of the Act).
A DATA Scheme entity may be subject to a civil penalty of 300 penalty units if it does not comply with these requirements (see sections 36(1) and (2) of the Act).
DATA Scheme entities must take steps to mitigate any harm from data breaches and suspected data breaches as soon as practicable after the breach occurs (see section 36(3) of the Act).
Where a DATA Scheme entity reasonably suspects or becomes aware of a Scheme data breach, that entity should immediately take action to contain the breach and prevent further access to or disclosure of the data.
For example, a DATA Scheme entity may reasonably suspect a Scheme data breach has occurred if it becomes aware it has been the subject of a cyber security incident (as defined in the ASD Glossary) involving unauthorised access to Scheme data stored on its servers. The DATA Scheme entity should stop the unauthorised access, recover the information and/or shut down the compromised system.
Another example is where a DATA Scheme entity becomes aware that it has inadvertently disclosed Scheme data to an unauthorised recipient. To prevent further unauthorised disclosure of the data, that DATA Scheme entity should seek confirmation that the unintended recipient has securely deleted and no longer retains a copy of that Scheme data.
To assist with identifying strategies to contain a data breach, DATA Scheme entities should consider the following:
- the circumstances of the data breach, including the cause and extent,
- the nature of the data and/or Scheme data, personal or not,
- whether the data is still being shared, disclosed or lost, without authorisation,
- whether the Scheme data is held by more than one DATA Scheme entity (for example, where Scheme data has been shared with multiple accredited entities),
- whether other DATA Scheme entities systems could be at risk of being compromised,
- what can be done to secure the data, or stop the misuse, interference, loss, unauthorised access, modification or disclosure, and reduce the risk of harm to affected entities (including individuals), groups of entities or things.
Where personal information is involved, the DATA Scheme entity may determine the data breach is an eligible data breach under the Notifiable Data Breach (NDB) Scheme in the Privacy Act 1988 (Privacy Act). If this occurs, assessment obligations under the Privacy Act are enlivened, as well as obligations to notify affected individuals if the entity has reasonable grounds to believe that the data breach is likely to result in serious harm to individuals.
DATA Scheme entities should be careful that any evidence relating to the data breach is not destroyed. This evidence may help in identifying the cause of the breach, address risks and may help the Commissioner or other regulators when undertaking any required assessment or investigation.
The DATA Scheme entity should conduct a prompt assessment to identify the risks posed by the breach to individuals, entities or things, and how to mitigate these risks.
DATA Scheme entities should gather and evaluate as much information about the data breach as possible, to gain a holistic view of the incident and the types of harm that may result from the data breach.
DATA Scheme entities must take reasonable steps to prevent or reduce any harm resulting from the breach (section 36(1) of the Act). Whether steps are reasonable is a factual matter in the circumstances of the particular incident. It is an objective test that has regard to how a reasonable person, who is properly informed, would be expected to act in the circumstances. A prompt and effective assessment of the data breach is key to informing actions to mitigate harm that results or is likely to result from the data breach, after the immediate priority of containment.
For data breaches involving personal information, assessment obligations under the NDB Scheme in the Privacy Act apply to Scheme data breaches (section 37 of the Act).
Upon assessing a Scheme data breach, a DATA Scheme entity should consider whether it could take any further steps to reduce any potential harm to affected individuals, entities, groups of entities or things, in addition to actions taken during Step 1: Contain.
Notification of breaches involving personal data
Section 37 of the Act preserves the Australian Information Commissioner’s oversight of data breaches involving personal information through a mechanism that engages the Notifiable Data Breaches (NDB) Scheme under Part IIIC of the Privacy Act 1988 (the Privacy Act). For more information about the NDB Scheme, visit: About the Notifiable Data Breaches scheme - Home (oaic.gov.au)
The definition of ‘personal information’ under the Act is the same as its definition under the Privacy Act.
Default responsibility to undertake relevant obligations under Part IIIC of the Privacy Act lies with the data custodian (see section 37(2) of the Act) unless expressed otherwise in a data sharing agreement with an accredited entity that is also an APP entity (see section 37(4) of the Act).
An accredited entity that is party to a data sharing agreement must notify the data custodian who has responsibility under Part IIIC of the Privacy Act if it reasonably suspects or becomes aware that a data breach of that entity has occurred. This written notification must occur in sufficient time and contain sufficient detail to enable the data custodian to comply with its NDB Scheme obligations (see section 37(3) of the Act).
Where both the data custodian and the accredited entity are APP entities, the accredited entity, and not the data custodian, is responsible for undertaking obligations under Part IIIC of the Privacy Act when this is expressed in the data sharing agreement (see section 37(4) of the Act).
A DATA Scheme entity must also give the National Data Commissioner a copy of any eligible data breach statement it gives to the Australian Information Commissioner under section 26WK of the Privacy Act as soon as practicable, if the eligible data breach relates to Scheme data (see section 37(5) of the Act).
Notification of breaches involving non-personal data
A DATA Scheme entity must notify the National Data Commissioner if it reasonably suspects or becomes aware that a data breach involving non-personal information has occurred (see section 38(1) of the Act). ‘Non-personal information’ is information that is not personal information about one or more individuals. A DATA Scheme entity may be subject to a civil penalty of 300 penalty units if it does not comply with this requirement (under section 38(1) of the Act).
Information that has been de-identified for the purpose of being shared under the Scheme is non-personal information (see the definition of ‘personal information’ under section 9 of the Act). However, it is possible that a data breach may result in de‑identified information becoming re-identified, thus becoming a data breach involving personal information.
A DATA Scheme entity must notify the National Data Commissioner of a non-personal data breach as soon as practicable after the end of the financial year in which the breach occurs (see section 38 of the Act). A data code may prescribe different periods for notification. No such period has been specified, although it may occur in the future.
Reporting events and changes in circumstances affecting accreditation
Accredited users and ADSPs have an ongoing responsibility under the Act to report events and changes in circumstances to the National Data Commissioner that are relevant to its accreditation (see section 31 of the Act). Data custodians that are accredited users and/or ADSPs also have this responsibility.
A Scheme data breach is an event that is relevant to an accredited user or ADSP’s accreditation and must be reported.
For more information, see the National Data Commissioner’s guidance note on reporting requirements for Scheme entities Reporting requirements under the DATA Scheme | Office of the National Data Commissioner.
Data sharing agreement parties
DATA Scheme entities are expected to notify other parties to a data sharing agreement, particularly the data custodian, to mitigate harm resulting from the data breach.
How to notify ONDC
DATA Scheme entities can report Scheme data breaches to the National Data Commissioner through Dataplace using the ‘Contact us’ tile.
Entities reporting a Scheme data breach involving personal information must provide the Commissioner with a copy of the ‘eligible data breach’ statement submitted to the Australian Information Commissioner (see s 37(5) of the Act).
It is recommended that entities include as much information as readily available at the time of reporting the Scheme data breach, including, but not limited to, the primary cause and description of the data beach, steps taken to mitigate harm, and any applicable supporting documentation in relation to internal assessments and/or incident reports conducted.
A Scheme data breach may trigger notification obligations under other legislation, such as the Security of Critical Infrastructure Act 2018 (SOCI Act), and/or under state and territory laws. These obligations should be captured in data breach response plans.
Notifying ASD of cyber-related Scheme data breaches
Where a cyber security incident has caused a data breach involving Scheme data, notification to the ASD should take priority. All entities, not just critical infrastructure owners, are encouraged to report cyber security incidents to the ASD to enable the ASD to provide assistance and maintain an accurate threat environment picture.
DATA Scheme entities may have notification obligations to the ASD under the SOCI Act if a data breach was caused by a ‘cyber security incident’ (as defined under the SOCI Act) affecting critical infrastructure.
Part 2B of the SOCI Act outlines mandatory reporting obligations for specific critical asset classes to report certain types of cyber security incidents.
To help you meet your cyber reporting requirements, the Single Reporting Portal | Cyber.gov.au brings together Commonwealth legislative reporting requirements that could be triggered by a cyber security incident.
DATA Scheme entities should conduct a post-incident review to identify and address any vulnerabilities in data handling that contributed to the incident, and improvements to the incident response process.
The review step should include:
- conducting a post-incident review with all the key internal and external stakeholders involved in responding to the data breach. This can identify gaps and vulnerabilities in the DATA Scheme entity’s information security processes and systems
- improving organisational data security processes and systems and staff training based on the findings of the post-incident review
- consulting with relevant committees and process/risk owners to implement prevention plans to prevent future incidents
- reviewing and updating the data breach response plan to reflect lessons learned
- testing the data breach response plan with hypothetical data breaches at all levels of severity and evaluating the effectiveness of the plan to ensure it is fit for purpose.
Useful resources For more information about the Notifiable Data Breaches Scheme, see OAIC's guidance: About the Notifiable Data Breaches scheme | OAIC For critical infrastructure owners, visit the Cyber and Infrastructure Security Centre for more information on obligations under the SOCI Act. Obligations under the Act still apply, but compliance with the SOCI Act takes priority. |
Seeking further advice
This guidance provides general information and is not legal advice. If you are uncertain about your obligations or are not sure how this guidance applies to your situation, you should seek your own professional advice. If you have a general enquiry about this guidance, you can contact us.
Guidance note 2023:4
First published: 31 March 2023
Last updated: 2 August 2024
